What is Biometric Authentication?
The earliest form of biometrics was the use of fingerprints to identify criminals. It was also used to sign contracts as each fingerprint is unique. But over the years, biometrics has been more and more important in technology too. Biometric authentication ensures the highest form of security across products and services. Specifically, it is the use of specific physical features– like your fingerprint– to verify a person’s identity before giving them access. Biometric authentication compares any given data to previously validated user data that is stored in a database.
The Global Identification Market is currently worth $8.6 billion as of 2021 and is expected to grow into an $18.6 billion market by 2026, with a CAGR of 16.6%. The biometric field within the market is expected to grow the most during that time period. This is because companies want to utilize biometric testing as it is faster and more convenient for customers and employees to verify their identity. It’s also harder for fraudulent activity to occur as every set of biometrics is unique to one person making it nearly impossible for someone to access someone else’s information.
There are many different types of biometric authentication–
Fingerprints
Every single person in the world has a set of fingerprints that is unique to only them. This makes fingerprints one of the easiest and best ways for companies to validate the identity of individuals. Companies like Apple and Samsung have implemented fingerprint scanners into their cellphones for a number of years as a better method of authentication for their users and can also be used to access certain apps like Venmo, Apple Store, Google Play and various banking apps. SecuGen, a well known company in the fingerprinting industry, has sold scanners used around the world for the purpose of information security, immigration, financial transactions, and more.
Vendors in the Field: HID, Suprema, NITGEN, CROSSMATCH, SecuGen, MorphoTrust, Aratek, Infinity, ABC INC. GenKey
Facial Recognition
Facial Recognition identifies a person using a digital image or video stored on a database beforehand. Facial Recognition works by comparing the facial features of someone such as nose shape and eye distance to a database of images and videos. This method of biometrics has been used for years by police agencies to look for missing people and catch criminals and more recently it has replaced the use of fingerprints as a way to unlock smart devices. Socure is one of many companies within the facial recognition industry, that recently released a new platform to help ease the process of onboarding. The platform allows an end-user to confirm their identity by submitting a selfie of themselves and copies of their official identity documents and uses facial recognition to verify the users identity.
Vendors in the Field: OnFido, Mitek, Idemia, BioID, IrisID, IDR&D, Paravision, Aratek, Infinity, Socure
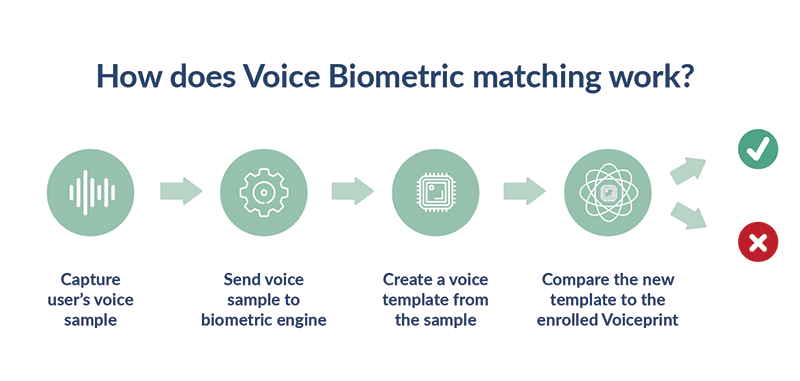
Voice and Speech Recognition
Voice & Speech Recognition like many other biometric systems works by comparing the voice, rhythm, pitch, and tone of someone to a multitude of voices stored on a database. Common types of voice and speech recognition systems analyze speech naturally and can verify who is talking and what is being said or can verify specific phrases. Voice and Speech recognition has been used in numerous services like Google Assistant and Siri. Last year, Amazon Web Services released Amazon Connect Voice ID for call centers to verify a customers identity. The service takes a 30 second recording of a customers first call to create an initial voice print and then compares any other calls a customer makes to the voiceprint to verify the identity of a customer while assigning a risk score so that an operator can intervene when necessary.
Vendors in the Field: Dragon, Google Assistant, Google Docs Voice Typing, Siri, Cortana, Speechnotes, Phonexia, IDR&D
Iris Recognition
Iris Recognition is another form of biometric verification that compares distinctive characteristics and patterns found in the colored part of someone’s eyes. Many organizations that use Iris Recognition are government programs like Border Patrol, Homeland Security checkpoints at airports, and police departments. However, more recently we have seen an increase in the usage of iris recognition in everyday life. Recently, Princeton Identity introduced iris scanners with plans to incorporate them into many facets of our life like office buildings, financial service centers, universities, and more. Their plan for this technology is to ensure the safety and protection of both people and data while restricting access from unwanted people.
Vendors in the Field: IRIS ID, CMI TECH, Princeton Identity, Sensor Access Technology
*There are also many other vendors in the field working on different types of authentication like DocuSign, Jumio, and Regula focusing on Document Authentication.
What does Biometric Testing solve?
Biometric validation benefits both the companies that implement the system and the users of those systems. This is because it is more secure since every person has their own unique set of biometrics. It is convenient and fast for users to authenticate themselves as they don’t have to remember numerous passwords and can just use biometric login. It also improves security for companies. With biometric authentication, companies can prevent information like passwords from being hacked or restrict access to information since biometrics are non-transferable.
Biometric authentication is important because it ensures that the action is being taken by a real person (and not a bot). It also confirms that they’re the right person, instead of a hacker, because the biometric information confirms who they are. This stops individuals from acting on behalf of others without their permission, creating false identities, or committing fraud.
Continuous Authentication
While biometric and traditional verification stops most instances of fraudulent access, it does not completely prevent all occurrences. Continuous authentication is another form of verification that is constantly validating a user’s access. The biggest thing continuous authentication solves for is the common act of people leaving computers, phones, and workstations unlocked and unattended. To prevent unwanted access, continuous authentication is constantly gathering data on a validated user’s actions and their patterns such as their typing speed, mouse movement, geolocation, and login time.
Based on this learned behavior, a system can validate a user continuously with machine learning and flag behavior that is considered inconsistent and prompt a user to reverify themselves. Biometric verification paired with continuous authentication increases security even more. For example, the usage of facial recognition or iris recognition can constantly validate a user when they are using a computer or smartphone on top of the already mentioned behavioral patterns.
Here at 3Qi Labs, we have undertaken several types of projects in the Biometric and Continuous Authentication field working with many of the leading companies mentioned in this post to conduct their tests and field studies and contribute to building their products. We also have expertise in conducting spoof tests and automating tests across a variety of Authentication Platforms. Please don’t hesitate to reach out if you are interested in working with us.